METHODOLGY Part 3
CLIENT/SERVER SIDE ATTACKS and other tests: here we distinguish attacks which occur via browser from malwares which infect the system:
NB.As some vulnerabilities could be patched as soon as possible, the tests are run on Windows XP2 updated until the end of 2005 only.
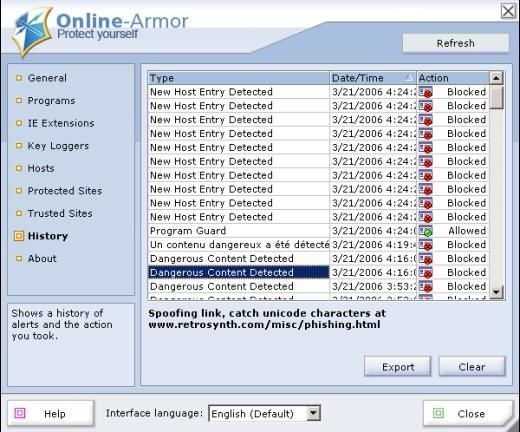
11.URL obfuscation: at http://www.retrosynth.com/misc//phishing.html
It is here basic techniques of Web spoofing and URL obfuscation (and easily detected):
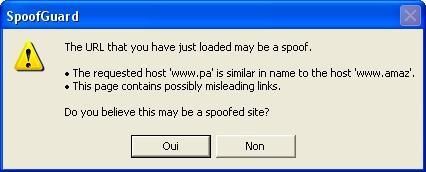
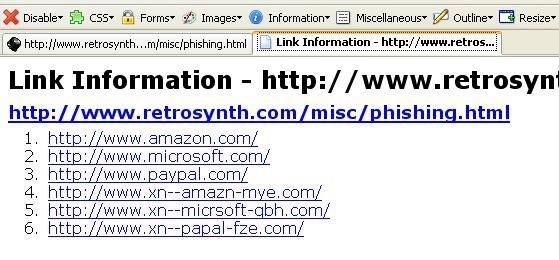
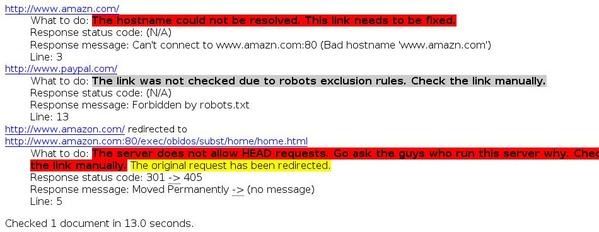
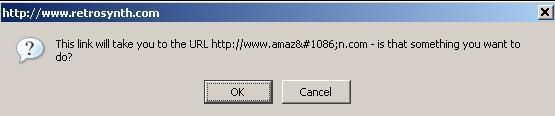
This attack is mostly used in Phishing and is really frequent: recently, i've received a mail for a Paypal account that i've never had, and the link redirects to another site than Paypal.
Online Armor is a personal HIPS which provides an efficient antiphishing protection:
12.Internet Explorer Exploits:
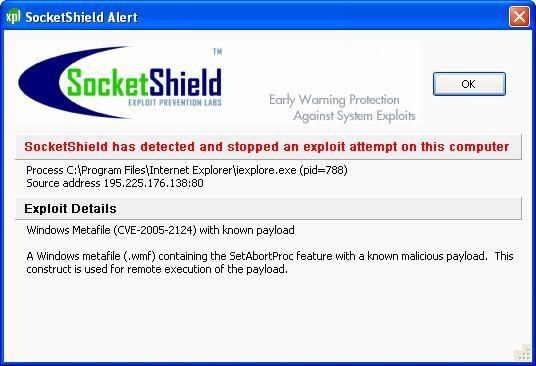
A new and interesting protection against zero-day exploits for home users is SocketShield (currently in beta): interesting application for users who are not surfing with a reactive antivirus (Kaspersky, BitDefender, Nod32 are for instance very reactive against exploits).
But unfortunately, there's no vaccine and efficient product against zero day/hour exploits and malwares.
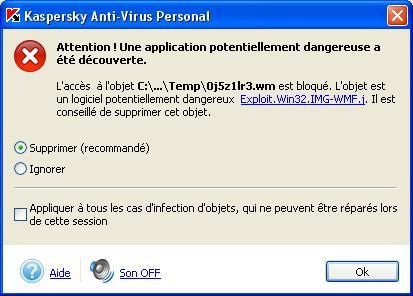
a.WMF exploits (on an unpatched machine)
-at http://sipr.net/test.wmf (example provided by the SANS Institut):
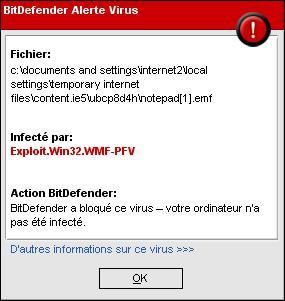
-at http://testing-onlytherightanswers.com/notepad.tiff
-at http://testing-onlytherightanswers.com/notepad.emf
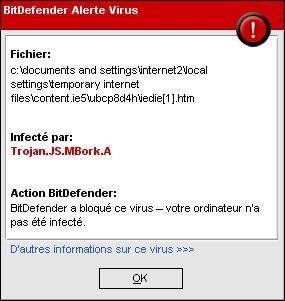
b.Recent and currently (29/03) upatched (fixes exist by Eeye and Determina) vulnerability:
All the test on this page:
-http://testing-onlytherightanswer.com/iedie.html
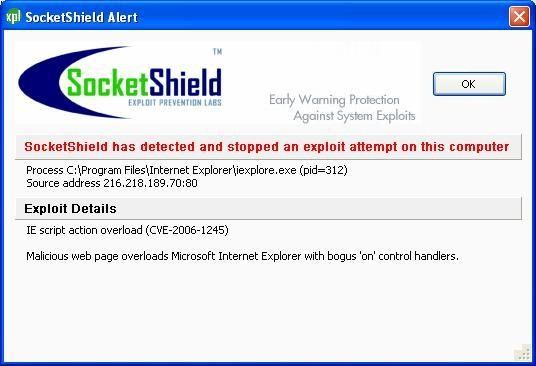
-http://testing-onlytherightanswer.com/TextRange.html
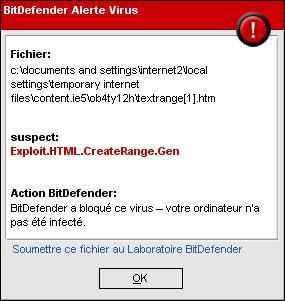
-Other variants using various methods (Tks to Nicolas): the site is a warez domain hosted in Russia:
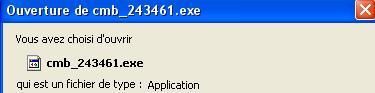
The downloaded file above is known by antivirus as a variant of trojan Small.
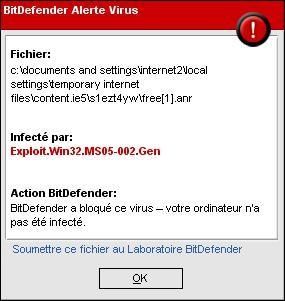
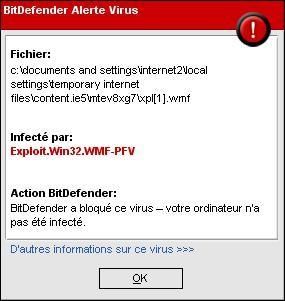
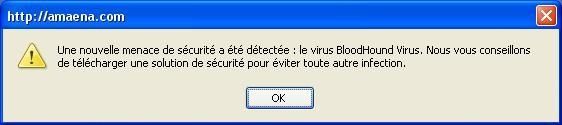
As usual this kind of site provides popups for suspect products (WinAntivirus in our case) as it shown above.
Translation: "A new security threat was detected: the BloodHund virus.
We recommend to download a security solution to avoid any infection."
13. Firefox exploits:
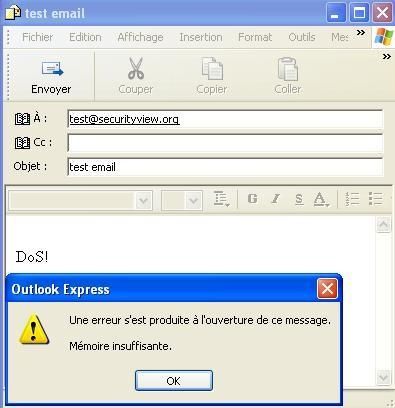
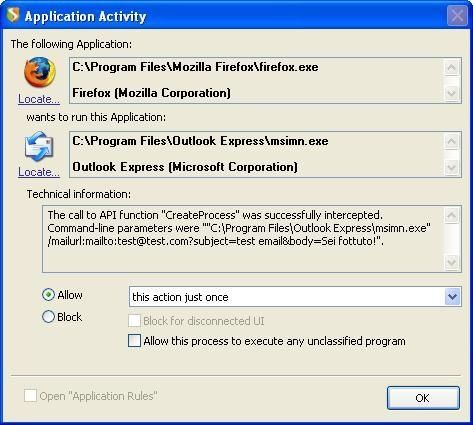
a. Firefox Dos Exploit
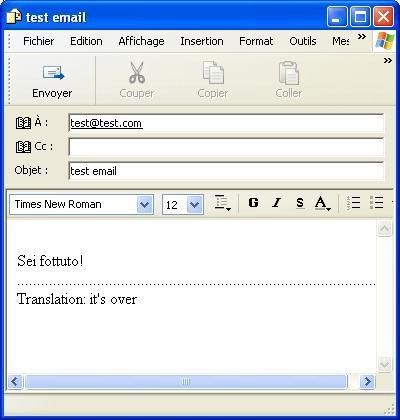
This exploit (by P4) via java script opens Outlook as it shown on its profiling here.
A few info about it here.
-at the original POC: http://geocities.com/werterxyz/test2.html
-at http://securityview.org/test.html
Simple countermeasures: disable java script in the browser options or use NoScript extension for instance:
It's also helpful to use an HIPS (here System Safety Monitor):
or a tool which has the ability to deny creation of thread/process like IceSword and Winsonar for instance both free), or Sandboxie which can mitigate the impact of the exploit:
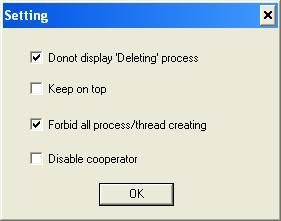
NB. Even if the marketing presentation of SocketShield claims that it is updated every 5 minutes, i've seen no alert from, neither by the antivirus: trusting in the "dear prudence" is often more reliable to mitigate the risks.
If a microsoft application is not used, it's suited to deny access (control panel, permissions).
b.Link of Death (Tks to Tobias): a simple script which blocks the browser:
http://www.arlt.com/shop/index.php?notfound=true%3Cuage=deutsch&searchword=%3Cscript%3Ewhile(1)%20alert(%27bub%27)%3C/script%3E
14.Finjan tests:
a. crashing Internet Explorer:
http://212.143.183.4/finjan/objects/MCRC/DosDemo.htm
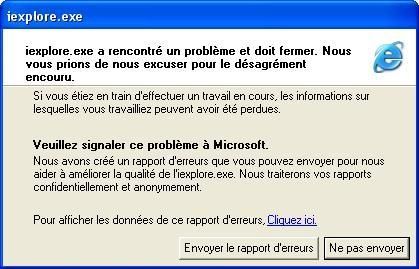
The tracking (but too long to be totally published) of this test is available here
b.Remote code execution via script:
http://212.143.183.4/finjan/objects/MCRC/VBDemo.htm
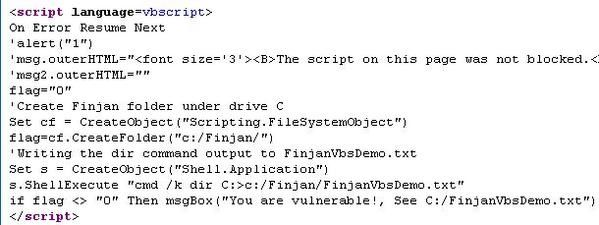
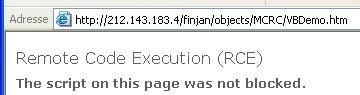
NB. for Firefox users, this kind of attack is easily blocked (in case of Scriting enabled) with NoScript extension:

NB. an interesting software for IE addicts is Spywall which tries to prevent some IE exploit (via Buffer Overflows for instance)
14.Windows account and privileges protection
Once an attacker has gained access to a machine (remotely or with a phisical access), he can easily hide an account if the host is not highly hardened.
-a.With AjouteUser (R) via CMD:
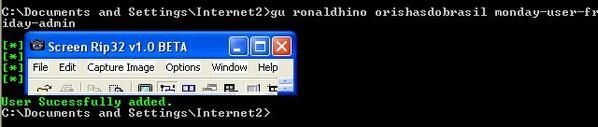
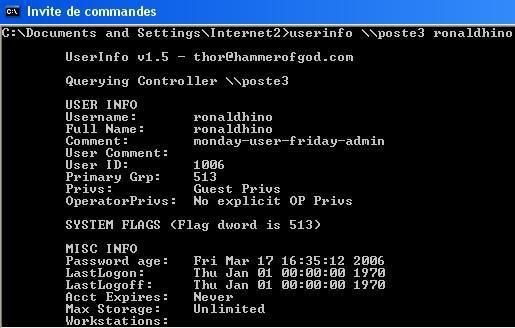
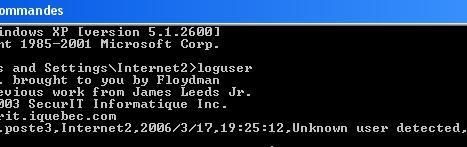
And no one of these accounts can be seen in the control panel:

-b.Shatter attack:
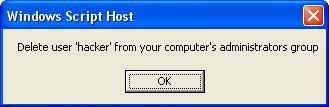
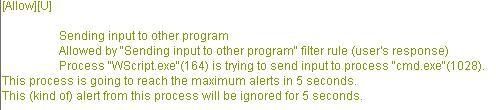
With a simple script (vbs), we create an hidden account (called "hacker"): the goal is to note if the HIPS has the ability to prevent the creation of this account.
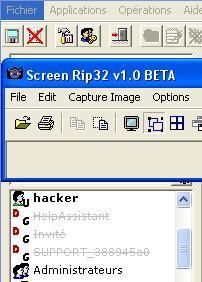
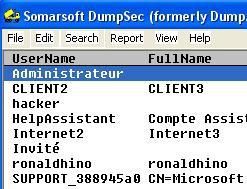
c.privilege escalation protection
-with Privdropper:
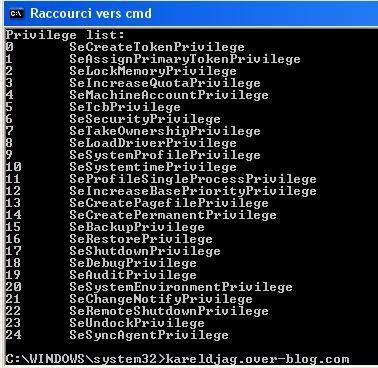
Privdropper is a tool wich can disable some privileges by writing and save it via the registry.
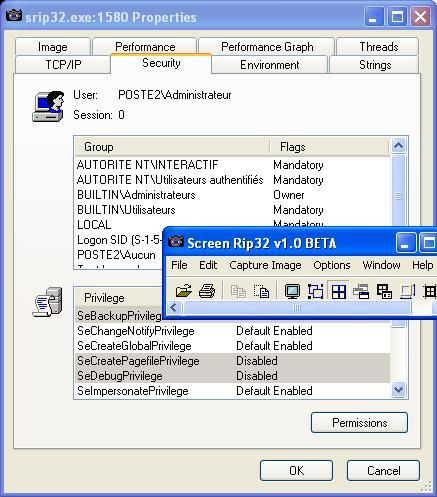
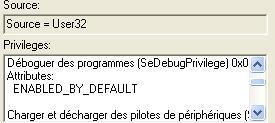
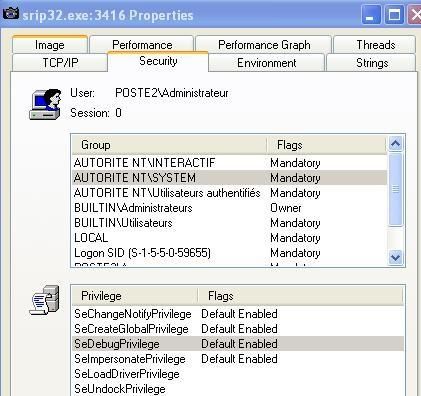
In our test, we'll try to disable SeDebugPrivilege.
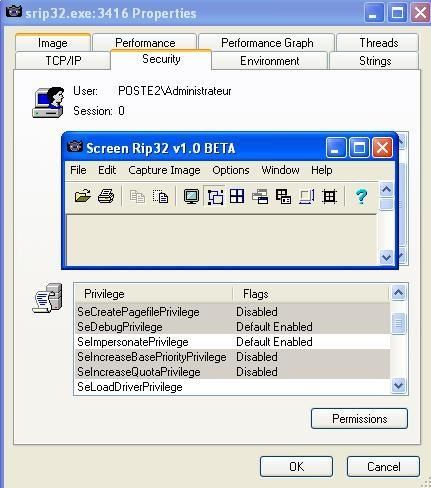
Here's for instance srip32.exe privileges shown by processexplorer:
And here the list of privilge which can be disabled with Privdropper:

-with Fu rootkit we enable SeDebugPrivilge in a process which has this privilege disabled (in hips.exe):
Exemple with srip32 before (see the image above shwown by ProcessExplorer) and after the privilege escalation via Fu:
d.with fu: adding new group of local SID on a process (hips.exe or srip32.exe):
Here an example with srip32 (renamed as kareldjag.exe) with KARELDJAG and SYSTEM:
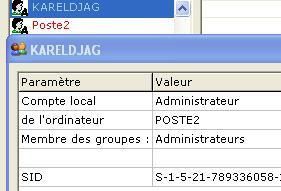
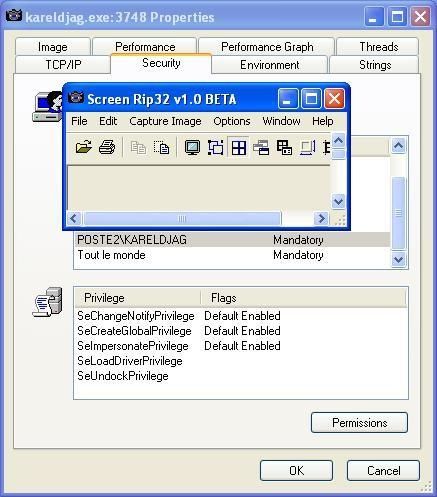
NB.the goal of these attacks is to gain administrator rigths and then more possibilities of system subversion and masquerade.
15.Man-In-The-Middle Attack:
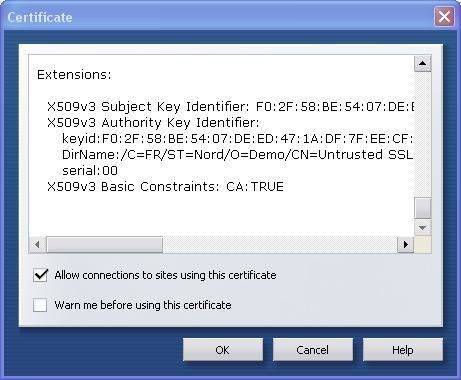
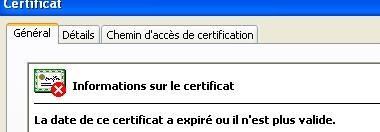
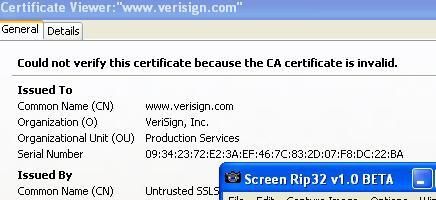
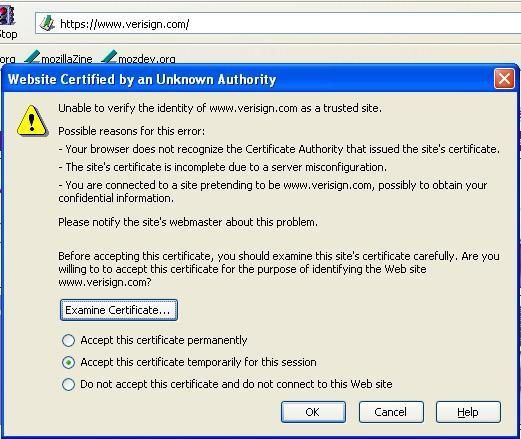
a.Here we use SSLSpoofer (Renamed), an HTTPS proxy which acts as a Man-in the-Middle between tha local host and the remote server, and returns an invalid or spoofed certificate each time an HTTPS connection is established.
The goal of this test is to note if the HIPS can prevent or detect the spoofing of the certificate.
Here's an example with Opera which detects this attack on Mozilla.org domain:
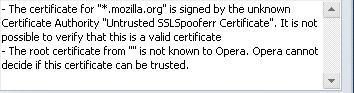
Another example with IE and mozilla on http://www.verisign.com/ :

b.with SSLAGY(R)
This is a proof of concept tool which demonstrates an HTTPS Man in the Middle via Internet Explorer by using API hooking.
NB.For the convenience of these tests, the files are run locally; and an efficient Man in the Middle often requires a DNS spoofing attack (case in some phishing attack, see the document "Phishing exposed").
17. Remote Access tests (tests done in a private LAN):
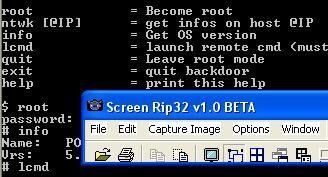
a. via a backdoor: we connect to the backdoor (detected by none antivirus on virus total) via a telnet access from the computer A to the computer B.
b. via an attack against VNC server: here we crack the weak (for convenience reasons!) password and connect to the computer B (we use a specialized cracker, or a recent and well known password cracker):
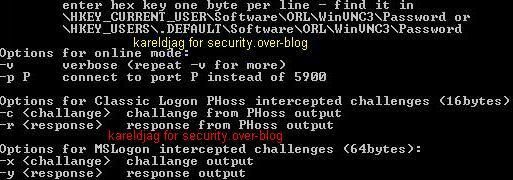
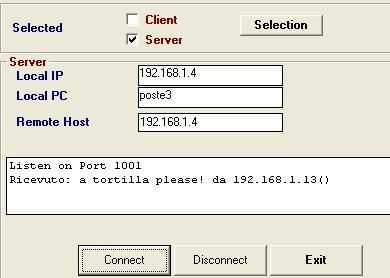
c. via an UDP Remote administration tool:
Here we connect to a R.A.T via udp protocol:
18. Data theft tests
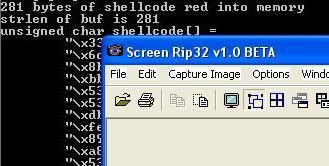
19. Buffer Overflow test
We just launch a buffer overflow and take not of its detection or not.
20.Other objective criteria:
We take into consideration important criteria for the potential customer or consumer via a rating (A, B, C, D, E and +-):
-installation: easy, fast, no reboot=A,
-ease of use: A if the product is already higly configured by default,
-convenience: A if the product works silently in the backgroung without disturbing the user,
-price: A if P<30 $/E, B if between 30 and 40, C if between 40 and 50, D if between 50 and 60, and E if >60,
-memory usage: - if it need too much CPU, + if it does not alter the performance of the computer (not excessive)
-laguage pack:+ for three languages for instance, --- for only one,
-support:+ if there is a forum, - if there's no one,
-privacy violation: ( from C if the program is intrusive).
Resource and Papers
-For more information about malwares used for this test:
Kaspersky encyclopedia
Online research tool (query for 11 databases at the same time)
A little summarize abou malwares: "Trends of Spyware, Viruses and Exploits" (pdf)
-About phishing and keyloggers:
Antiphishing Group web site
One of the most exhaustive paper (pdf) about phishing: 'Phishing exposed' here
About keyloggers and virtual keylogging
An example of a server side protection against virtual keyloggers with K-Defense.
IDTheft is a real problem, and frequently, magazines alert users about this phenomena like here or here.
-About Cool Web Search pests and spywares in general
-About rootkits
-An example of SSL Man-in-The-Middle: (pdf)
(...........................................................................................................................................................)
