DEFENSEWALL TEST Part 2
Part II
In the wild with real malwares
7° Boot sector/Bios/MBR protection : MBR virus
DefenseWall does not provide boot sector protection, and most of all, its service/driver is not a boot start but a system start: consequently, the protection during the boot is limited. Failed.
8° Rootkit protection
a) Rootkit technology prevention: passed.
- hidden process: since DefenseWall blocks access to physical memory, we're unable to hide test.exe:
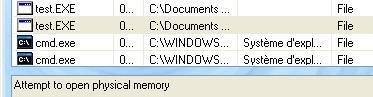
- hidden service/driver: DefenseWall blocks the creation of the service:
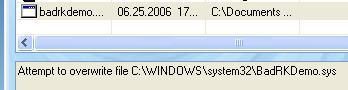
DefenseWall has not the ability to detect hidden objects.
- hidden process: DefenseWall does not display the hidden test.exe in its trusted or untrusted list as it is shown by this image (test.exe is marked in red as hidden by DarkSpy):
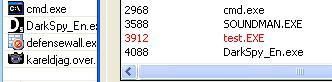
- hidden service/driver: DefenseWall can't detect the hidden service/driver.
NB.Currently, most rootkits detectors are bypassed by this demonstration tool.
c) Rootkit detection with HackerDefender: Failed.
DefenseWall does not detect objects hidden by the rootkit already installed.
DefenseWall task / DarkSpy task
NB : DefenseWall and HackerDefender are "sharing" some addresses/Nt functions in the System call table, thus HackerDefender is unable to load after a reboot : The driver file is still there, but the service is not running anymore. DefenseWall gets the upper hand, and the rootkit's files are not hidden anymore (nicM).
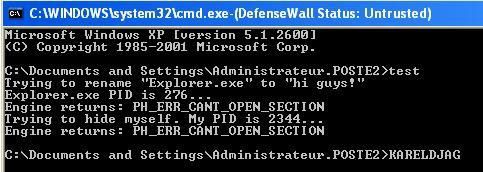
d) Rootkit prevention with Fu : passed. Via a command line, we're unable to install and hide the rootkit because DefenseWall blocks its driver from loading.
9° Protection during the boot and before the shutdown
a) Keylogging protection
* With WinlogonHijack : CMD and injector are run untrusted: the code injection in Winlogon is prevented by DefenseWall: passed.
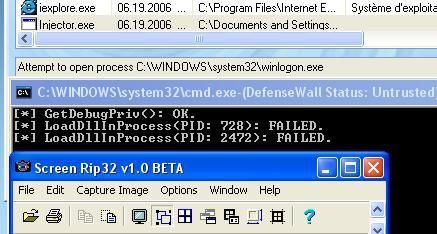
If the test is run with DefenseWall disabled, this last one is unable to prevent the login informations from being copied to a log file.
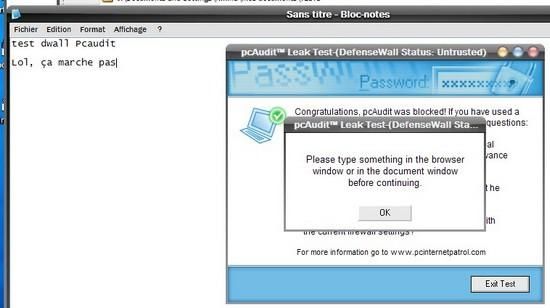
* With Zkeylog : This keylogger doesn’t work from a removable device, as a CD, so that it was launched from C, from an ‘untrusted folder. DefenseWall does prevent it from installing its global hook, then the keylogger doesn’t record anything (PIC 2) : Passed
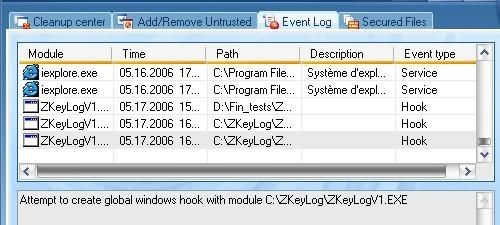
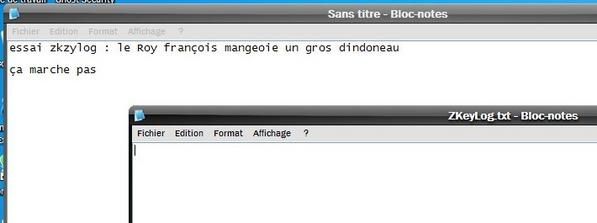
b) New program running at the boot
* With Ardamax keylogger : Ardamax setup file was downloaded directly from its web site, then was automatically launched ‘untrusted.
After installation, the keylogger doesn’t work :
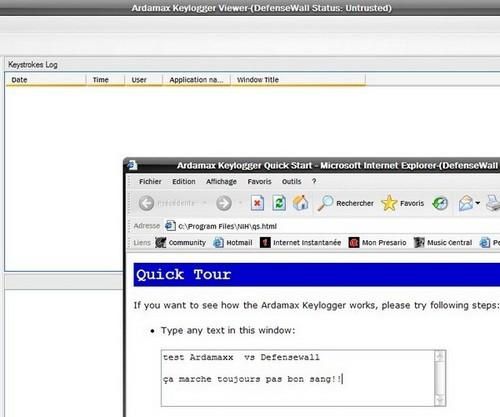
And it doesn’t restart at all after a reboot. Passed
* With MakeService : As this test is made with the protection disabled, the service can be created, after a reboot DefenseWall will show its process in the Trusted/Untrusted processes panel; if the service is running.
* With EyeBootRoot : This rootkit/backdoor patches the OS (NDIS.sys) just after the bios, and just before the start of Windows: DefenseWall, which starts with Windows can't prevent and detect this rootkit backdoor: Failed.
c) Program running before the shutdown
* With RunatExit : The .ini file is set to launch HackerDefender at exit.
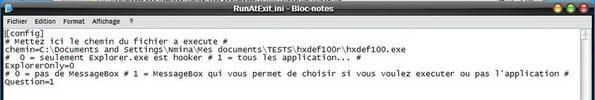
Note that when RunatExit is started, cmd.exe is ‘untrusted too :
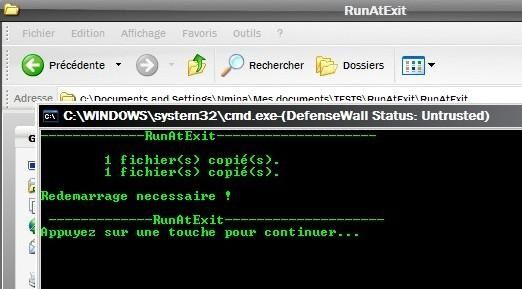
But when I press the touch to restart... nothing happens, DefenseWall did prevent it to launch at exit. Passed.
I had to make the test without DefenseWall to see what’s happening when the program works :
10° Keyloggers/Message hooks protection
a) Keyloggers installed with DefenseWall disabled
* With KGBKeylogger : The stealth version is working, as expected.
But although the keylogger is supposed to be stealth, we can actually see its process within DefenseWall's control panel – including it’s funny icon :
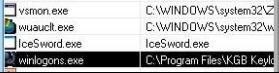
And the user can kill the task within DefenseWall panel. But of course, DefenseWall doesn’t prevent the keylogger to record keyboard strokes as long as it is running.
* With QuickKeylogger : Once installed ‘trusted, and the computer rebooted, the keylogger is working :
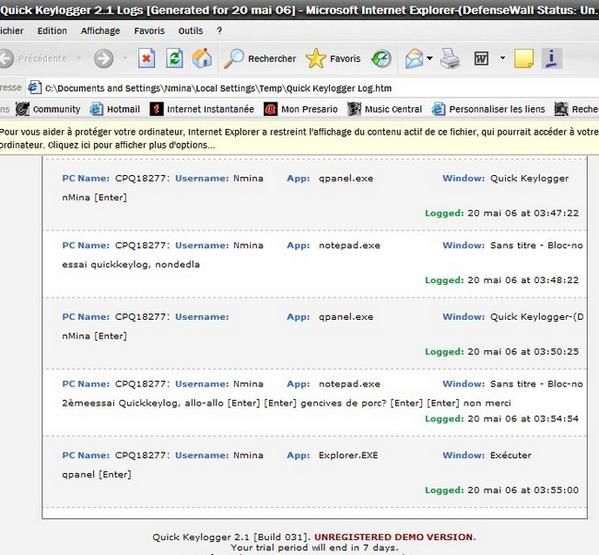
But one particularity of this program is that it is using IE for its controls. Then, the process (qpanel.exe) was set as ‘untrusted (as IE), when I disabled/re-enabled it, for instance; so some actions were prevented by DefenseWall :
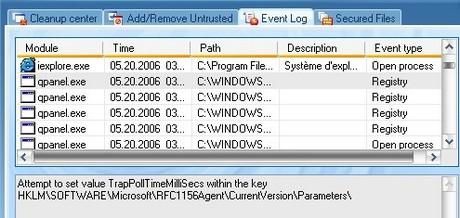
It didn’t prevent the program to record keystrokes however, since keylogging is done by the fake SVCHOST.exe. Then a inquisitive user could notice this fake service, because the path of this SVCHOST.exe is showing in DefenseWall (it’s Windows/System, instead of Windows/System32) :
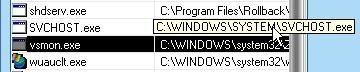
But DefenseWall doesn’t allow to kill the service. Then DefenseWall can allow to detect it, but can’t prevent it to record keystrokes (the only time it’s clearly showing up in DefenseWall is when the “bad guy” who installed it is opening the program’s logs and controls – obviously not something the “victim “should do).
b) Virtual keyboard keylogging
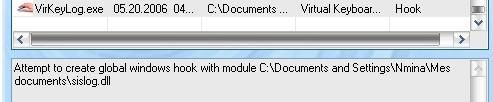
The virtual keyboard is started, then VirKeylog is started too, ‘untrusted (it couldn’t run from the CD, I had to launch it from C) : DefenseWall does block the global hook. Nothing is recorded from the virtual keyboard : Passed
c) PC Audit 6.3 test
The file is downloaded from the website, so that it’s launched ‘untrusted automatically. The two DLLs are blocked from setting a global hook :
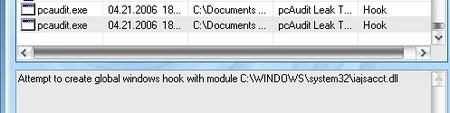
Then nothing is recorded from the keyboard : Passed
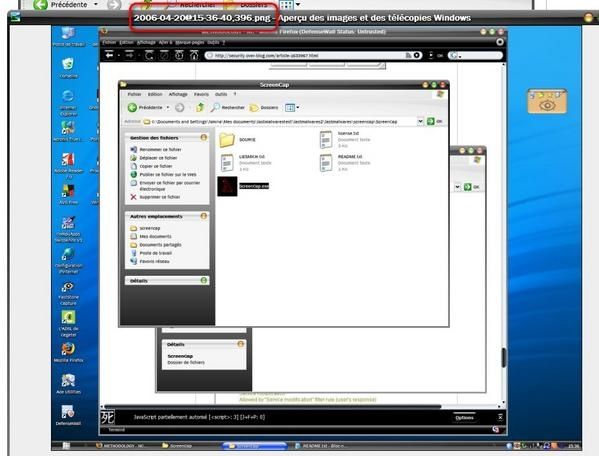
d) Screencap test
Screencap is launched ‘untrusted (but from C, not form CD, since it does need to record the screenshot it takes in its folder), but it manages to capture the entire screen. Here is the pic it was able to capture : Failed
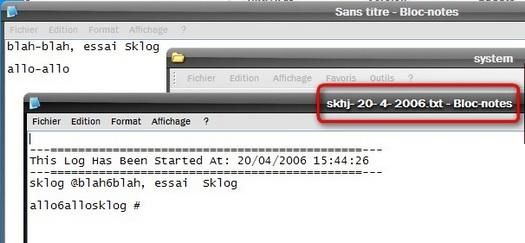
e) Sklog test
Launched ‘untrusted (from the test-CD), it carries on working : Failed
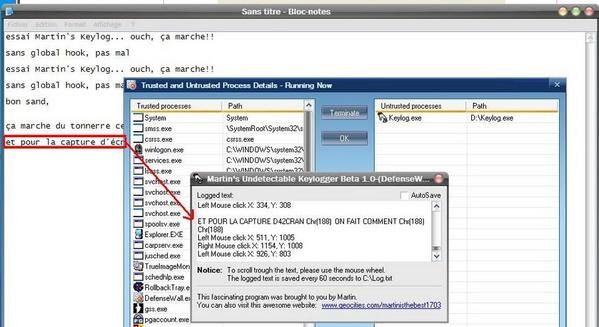
f) Martin’s “the best Keylogger”
Launched ‘untrusted, from the CD, it is able to record all keystrokes, without global hook warning from DefenseWall : Failed
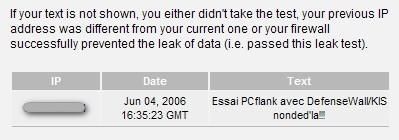
g) With PCFlank leaktest
The data is sent through IE : Failed.
11° Download protection
The design of DefenseWall is not to prevent anything from being downloaded : the file is downloaded, but is automatically added to the ‘untrusted files.
12° Malware protection
a) Trojans and backdoors
* With BasicBackdoor : The file is launched ‘untrusted, and listens on local connections. As the backdoor just do open a connection, nothing is blocked by DefenseWall. Failed.
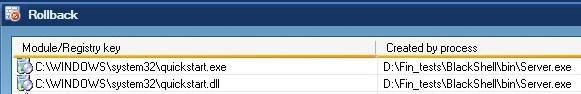
* With Blackshell : The backdoor is launched ‘untrusted, the file Quickstart.exe is started and tries to add a Run startup key, and to modify IE. Then IE is started in hidden mode, using a global hook, and listening on the local network (red connections mean “hidden”, the pic is from Port Explorer)
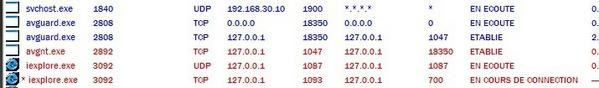
So the backdoor seems still active there, but everything was set ‘untrusted, under control (except the connections, but DefenseWall doesn’t deal with connections), and killed when pressing the “close all untrusted processes” button in DefenseWall.
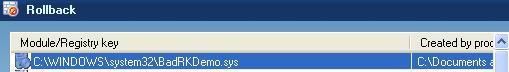
It looks like all modifications were blocked by DefenseWall, since the computer is “clean” after a reboot; nothing is restarted, and all files created are in the Rollback panel, ready to be deleted. (I say “seems”, because all blocked events were overwritten in DefenseWall’s Event log viewer : IE was launched by the backdoor, and then all IE entries did push the other entries out – the logs are size-limited). Passed
* With GasparHook : The backdoor tries to write on the memory of all processes running, which is blocked by DefenseWall : Passed.
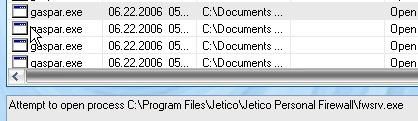
(When the test is not blocked, all processes running are killed : Antivir, Jetico, in my config).
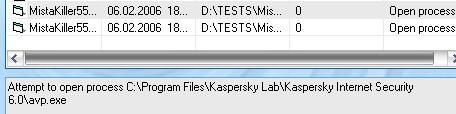
* With Mistakiller : DefenseWall does prevent it from terminating the AV (tested with 2 setups, AVG and KIS 2006, as in the pic) : Passed
* With Haxspy : The installer is launched ‘untrusted, all files created are set ‘untrusted too. DefenseWall does prevent it from changing XP firewall “white list” policy, and from installing the rootkit.
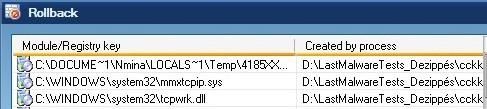
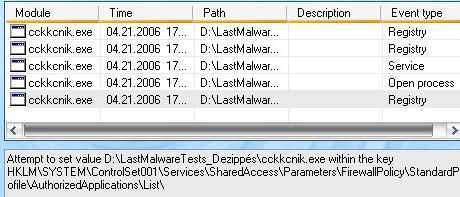
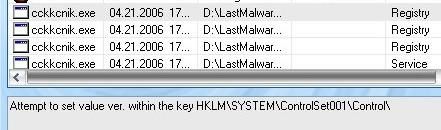
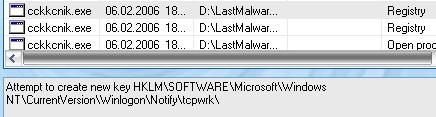
Then the mmxtcpip.sys driver is not loaded : the installer can be killed, and the files removed. But nothing survives a reboot anyway, even if files are left behind. Passed
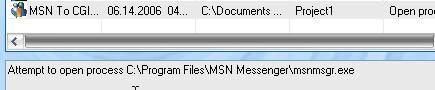
* With MSN to CGI : MSN to CGI doesn't manage to kill the real MSN running, and then appears clearly as a second and new instance of MSN : Passed.
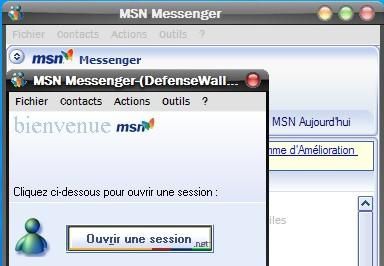
* With MSN pass sender : The fake csrss.exe message hooks are not detected and the program is able to send data to the preconfigured yahoo servers: Failed.
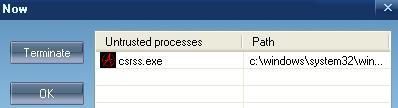
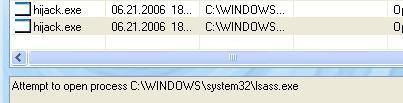
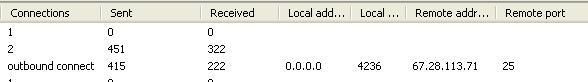
* With phping : DefenseWall was unable to detect ICMP echo/reply: Failed.
* With Registrator : The installer file connects to various sites, downloads and launch new files from various sites. Eg this one :
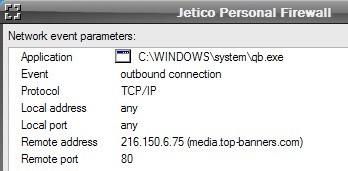
But all these files are of course ‘untrusted, and they fail to harm or to install the downloaded spywares :
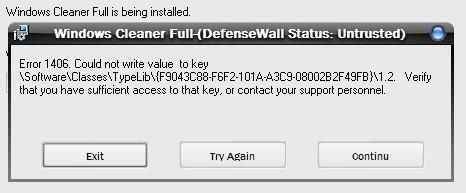
And qb.exe fails to register at startup (picture made during a second test, a few days later; qb.exe is now called “QBTool.exe”, and the payload was a new one) : Passed
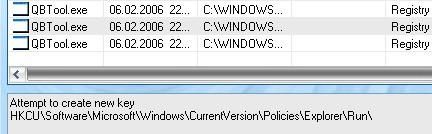
If all untrusted processes are closed, nothing survives, and IE is clean.
* With Tibs : The file connects to directplugin.com, download other files, all ‘untrusted. But since the payload changes very frequently, by the time I had a spyware installer downloaded, it was unable to install. Test Passed.
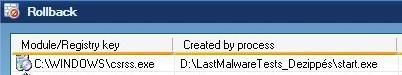
* With Start : Once started, the file stays inactive for 5-10 mn, then creates a file in Windows (csrss.exe), and tries to add itself to startup (two keys), and to modify HOSTS file. Everything is blocked, except the backdoor local connection : The csrss.exe file is never executed. Passed.
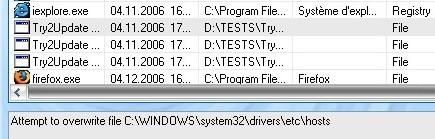
* With TryToUpdate : DefenseWall does prevent it to modify HOSTS file : Passed
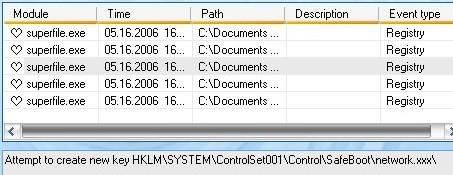
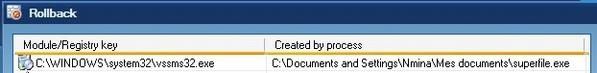
* With Turkojan trojan : The server (here “superfile.exe”) is blocked by DefenseWall from writing its entries in registry, and the file created in system32 is tracked. Passed.
* With Tx backdoor : This backdoor merely opens a connection, then nothing particular is blocked by DefenseWall. Failed.
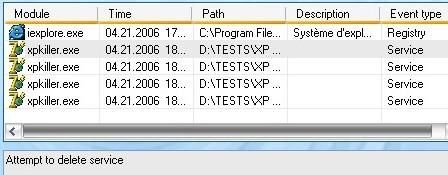
* With XP Killer : This file was able to stop automatic updates service, but DefenseWall did prevent the most harmful actions : no system files (auto updates service, XP firewall and restore service files) were deleted, so that the system state is normal after a reboot. Test not 100% passed, but not failed either : ½.
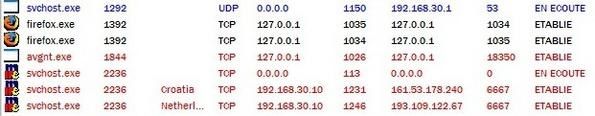
* With Zapchast : The so-called gif file is extracted untrusted, and opens a backdoor (svchost.exe). The backdoor is connecting here and there on the network :
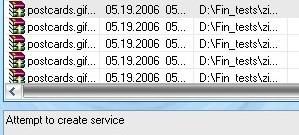
But the malware service couldn’t install, and registry changes were prevented. Passed.
