DefenseWall Test Part 3 Suite
15° Man-in-the-middle (MIM) attack test :
a. SSLSpoofer test:
Since the file needs a service to work, it is stopped by DefenseWall.
The spoofer has to be installed 'trusted to create and launch it's service, and to work; but as doing, DefenseWall is not supposed to prevent it.
If we take only in consideration the spoofing of the certificate, DefenseWall is unable to detect and block this kind of attack: failed.
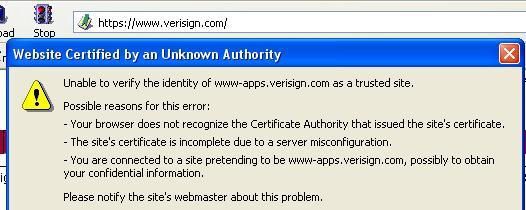
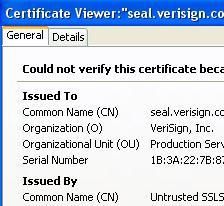
In the real world of this kind of attack, the majority of HIPS for end-users does not provide a prtection against this kind of attack (only Online Armor and Viguard Pro claim a DNS spoofing protection which is often used in combination with a MIM in phishing).
-with SSLagy:
CMD and SSLagy are run untrusted, and curiously, SSLagy does not appear in the logs.
When we try to jump from the start page (google.fr) to https://addons.mozilla.orh/ via a bookmark link, we get a blank page.
The https connection was hijacked by SSLagy, and DefenseWall was unable to prevent it: failed.
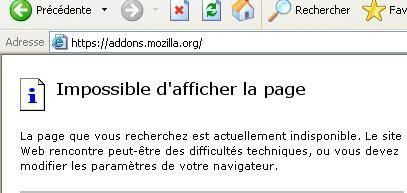
Ilya Rabinovitch answer: It is browser hijacker- it is firewall's job, not mine one.
NB. By using API hooks, SSLagy modifies Internet Explorer: since there's no integrity protection of the browser (especially against any kind of modification), the door is opened to many security issues (HTTPS hijacking in our case).
That's true that if the firewall blocks SSLagy, hijacking will not be possible.
But on the other hand: no IE modification= no HTTPS hijacking.
16.Other objective criteria:
-installation: fast, easy and requires a necessary reboot: A.
-ease of use: A: advanced knowledge is not needful unlike for most HIPS: since the concept is understood, the configuration should be easy.
-conveniences: the interaction DefenseWall/user is very limited: the computer is used without being disturbed: A.
-price: very cheap (less than 30 $ and 25 Euros): A.
-memory usage: not excessive, but also not perfect: B.
-language pack: only one (english): - - - .
-support: the user can found help in a dedicated and reactive forum: +++ .
-privacy violation: nothing suspect was noticed. Not intrusive at all: A.
All tests done by nicM, except for:
-launching calc.exe via shellcode,
-service interruption with Osrloader,
-MBR virus,
-Eeye Boot Root, WinlogonHijack and rootkit protection tests ( all by kareldjag, except for HackerDefender detection done with nickM),
-Phping backdoor,
-Worm P2P silly,
-privilege and account protection (with Privdropper, Fu and shatter attack),
-Man in the middle tests with SSLSpoofer and SSLagy,
-Objective criteria, in partnership with nicM;
by kareldjag.
OVERALL
a. SSLSpoofer test:
Since the file needs a service to work, it is stopped by DefenseWall.
The spoofer has to be installed 'trusted to create and launch it's service, and to work; but as doing, DefenseWall is not supposed to prevent it.
If we take only in consideration the spoofing of the certificate, DefenseWall is unable to detect and block this kind of attack: failed.


In the real world of this kind of attack, the majority of HIPS for end-users does not provide a prtection against this kind of attack (only Online Armor and Viguard Pro claim a DNS spoofing protection which is often used in combination with a MIM in phishing).
-with SSLagy:
CMD and SSLagy are run untrusted, and curiously, SSLagy does not appear in the logs.
When we try to jump from the start page (google.fr) to https://addons.mozilla.orh/ via a bookmark link, we get a blank page.
The https connection was hijacked by SSLagy, and DefenseWall was unable to prevent it: failed.

Ilya Rabinovitch answer: It is browser hijacker- it is firewall's job, not mine one.
NB. By using API hooks, SSLagy modifies Internet Explorer: since there's no integrity protection of the browser (especially against any kind of modification), the door is opened to many security issues (HTTPS hijacking in our case).
That's true that if the firewall blocks SSLagy, hijacking will not be possible.
But on the other hand: no IE modification= no HTTPS hijacking.
16.Other objective criteria:
-installation: fast, easy and requires a necessary reboot: A.
-ease of use: A: advanced knowledge is not needful unlike for most HIPS: since the concept is understood, the configuration should be easy.
-conveniences: the interaction DefenseWall/user is very limited: the computer is used without being disturbed: A.
-price: very cheap (less than 30 $ and 25 Euros): A.
-memory usage: not excessive, but also not perfect: B.
-language pack: only one (english): - - - .
-support: the user can found help in a dedicated and reactive forum: +++ .
-privacy violation: nothing suspect was noticed. Not intrusive at all: A.
All tests done by nicM, except for:
-launching calc.exe via shellcode,
-service interruption with Osrloader,
-MBR virus,
-Eeye Boot Root, WinlogonHijack and rootkit protection tests ( all by kareldjag, except for HackerDefender detection done with nickM),
-Phping backdoor,
-Worm P2P silly,
-privilege and account protection (with Privdropper, Fu and shatter attack),
-Man in the middle tests with SSLSpoofer and SSLagy,
-Objective criteria, in partnership with nicM;
by kareldjag.
OVERALL
