GASPAR Hooker Test
Result of online scans: the original file is detected by none AV on Virustotal, and the next image is related to the recompiled file as an .exe:

This file is a Proof of Concept trojan designed to illustrate some firewall evasion methods: it hooks via OpenProcess, VirtualAllocExe, WiteProcessMemory and CreateRemoteThread) of running applications and tries to bypass the firewall via wininet.dll (of allowed application like Internet Explorer).
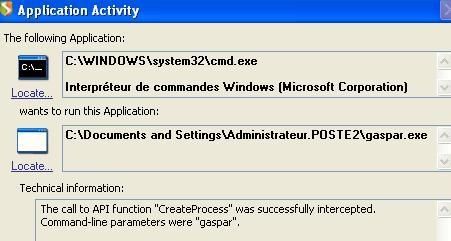


And with Jetico firewall:

And we get a spate of popup alerts of Windows Data Execution Protection (DEP, more info here and here) in relation to all running and modifed application:


