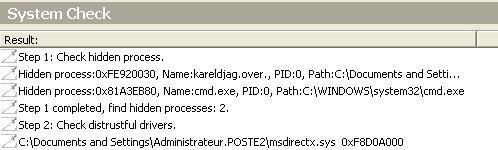
ROOTKIT TEST
Here we just illustrate some rootkit behaviours and show detection by some well known or not anti-rootkit tools.
For more information, it can be suited to take a look at the next version of my article which will be updated this summer.
NB.Srip32.exe is shown as kareldjag.over.blog.exe in some screeshots, just to prevent the use of these images in other sites or blogs: this article for instance seems a little bit similar to this one (included the example of locate32 tool)!
Writing an article without mentionning its sources is not ethical and profesional.
If we try to launch HackerDefender, it needs to load its driver:
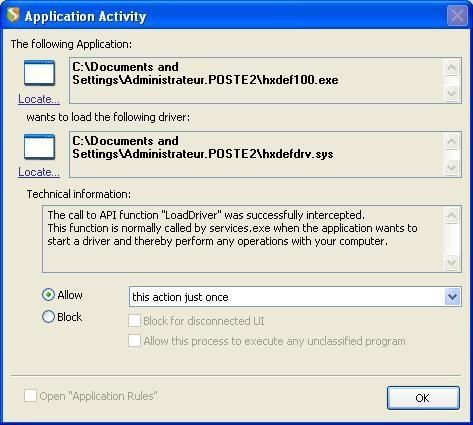
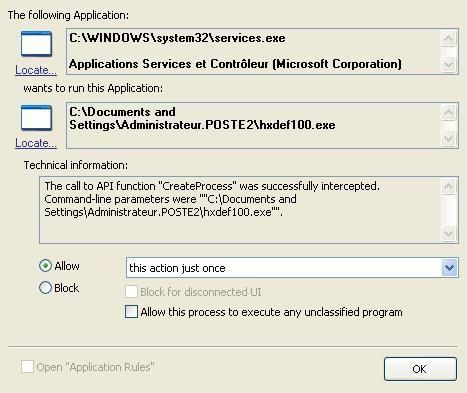
Then it begins to patch system's process to hide itself:
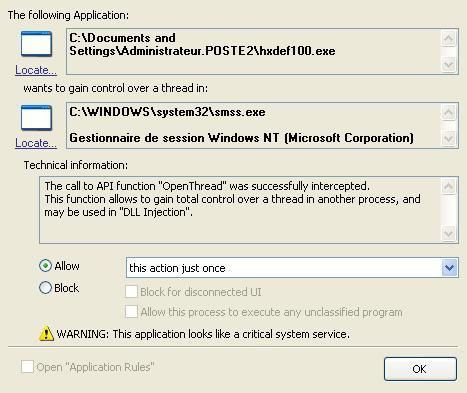
Here's the libraries hooked by HackerDefender:
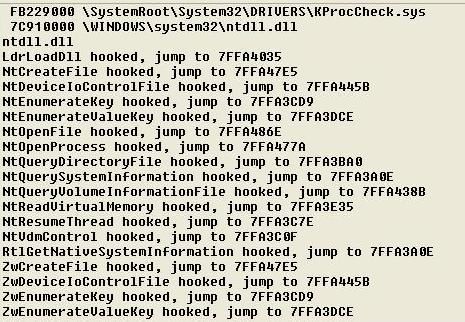
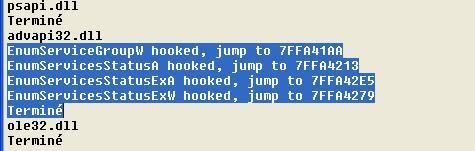
Here the hooked functions shows clearly that something tries to hide from the Service Controler Manager:
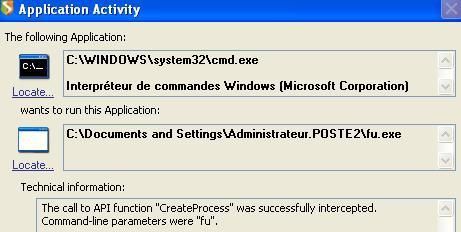
By using Fu to hide objects (drivers, processes etc):
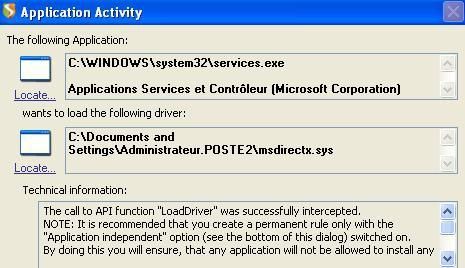
The detection of FU and HxDef drivers with Darkspy:
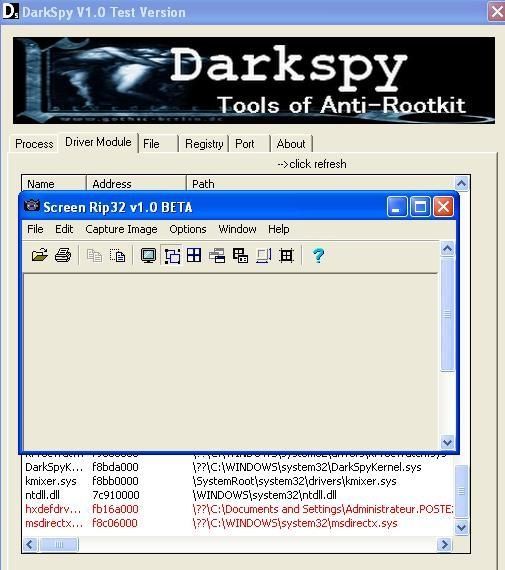
And here processes (Fu is represented by cmd.exe):
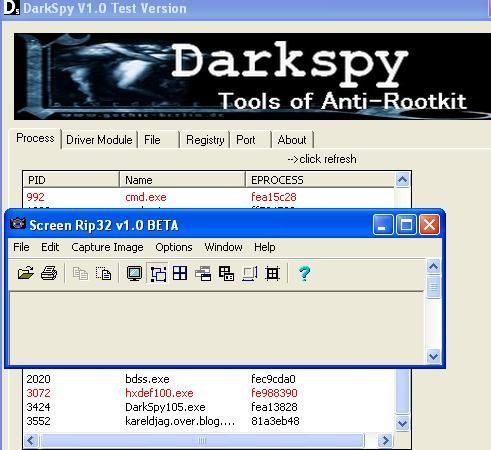
The result by IceSword:
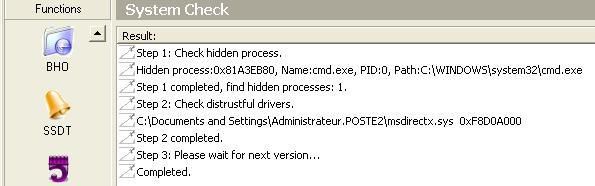
And here with another detector:
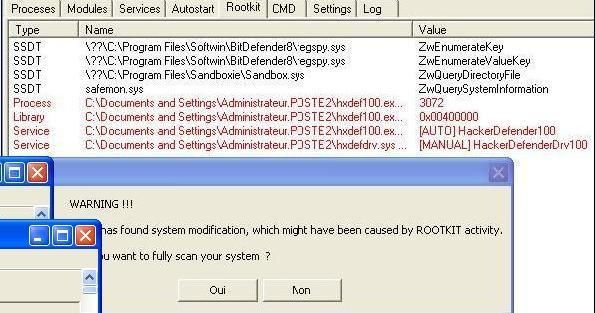
Now if we hide Fu and srip32.exe renamed as kareldjag.over.blog.com:
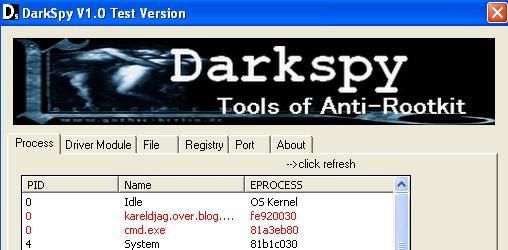
With another detector from Russia:
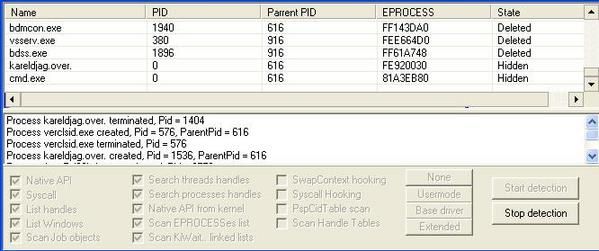
The result of the IceSword's check: