METHODOLOGY Part 2
PART 2: IN THE WILD WITH REAL MALWARES
7) Boot Sector/Bios/MBR protection: MBR virus
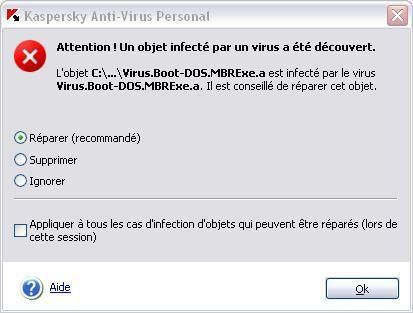
When a computer is not protected with a Bios password, and neither by an antivirus (only HIPS), an ill-intentioned person can easly boot the computer from external drives and cause damages.
This test just shows that a line defense based only on the HIPS, and without an antivirus, does not cover MBR/CMOS/Bios protection and risks.
NB.Viguard and Invircible are the rare HIPS which provide boot sector protection.
8) Rootkits protection (detection and prevention)
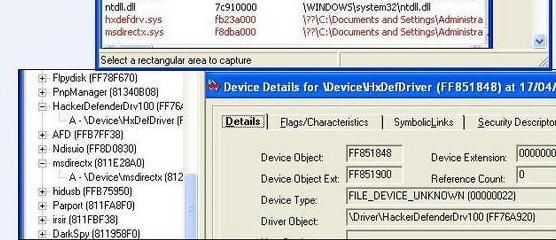
9) Protection during the boot and before the shutdown
Loading as a system start is a minimum for a security software (service, driver, and executable), but more efficient is a boot start kernel service/driver.
a) keylogging protection with WinlogonHijack :"This tool intercepts Winlogon logins by injection a dll into the winlogon process and logs the username, password and domain to a file".
-keylogger: with Ardamax Keylogger
-new service : with the HIPS disabled, we install a backdoor (released for a hacking challenge, and not detected by on Virus Total) that runs as a service and listening on 666 port.
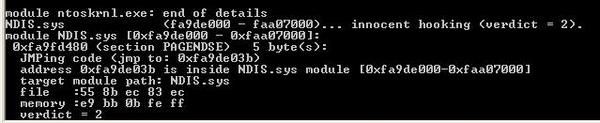
This proof of concept of boot sector rootkit loads and patches the system after the bios and before the OS: we boot from the ISO image via a CDRom.
Here's the patch of NDIS:
c) program running before the shutdown
In this case we use a program designed to launch an application when Windows is about to reboot or shutdown: during this phase, many security protection might be bypassed.
With RunAtExit , we just need to configure the Ini. file, and then to reboot.
Here we choose to run Hxdef.exe (HackerDefender rootkit) before the exit: if this event is not detected, the rootkit will survive at at the reboot.
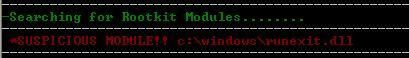
10) Keyloogers/Message hooks protection
a) We install a keylogger with the HIPS disabled ( or in DOS mode for instance) and reboot the computer ta take note of the keylogging protection.
Example with:
-KGBKeylogger, installed with the stealth mode activated.
-Quick Keylogger (we install it, and reboot to see if detected)
-ChatWatch (instant message monitoring soft): we launch Yahoo or MSN messenger at the reboot.
b) Virtual keyboard keylogging (we launch OSK, the windows virtual keyboard):
We run the keylogger and enable the capture (recorded in a log file):
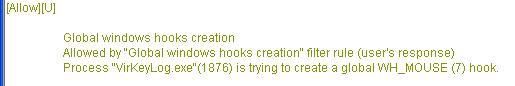
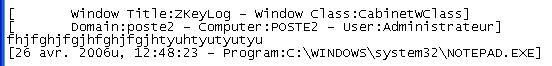
Then we type a short word (better for the screenshot) like ELVIS or ZIDANE for instance (here's the log):

NB.The test is run locally: results will be different (no possibility of detection via the HIPS) on a web server (bank web site) infected with a mailicious code.
Examples of online virtual keyboards here.
c) with PC Audit 6.3 (leaktest)
d) with Sreencap : this litlle tool can take a screenshot inside the folder (or on the web server) where it is executed: this kind of method is used by phishers to steal confidential data on legitimate or fake web sites (see Websensessecuritylabs reports for more information).
e) with Sklog
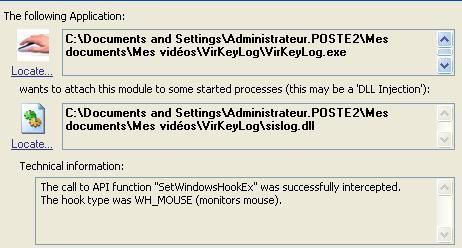
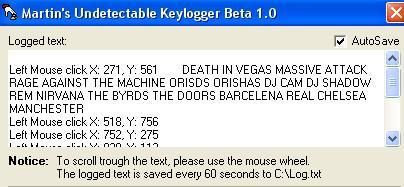
f) Martin's the best keylogger:
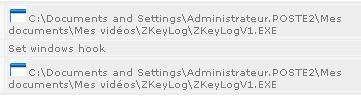
h) with PCFlank new Leaktest
11) Downloading protection:
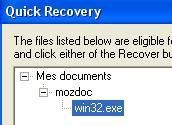
Here we'll see if the HIPS can prevent files from being downloaded accidentally (via a faked link) or legitimately: the image above illustrates Sandboxie which has the ability to protect the system from downloads.
We choose to download a simple screen capture tool like Srip32:
http://d.nardi.free.fr/D_NARDI/srip32.exe
12) Malwares protection:
a) trojans and backdoors:
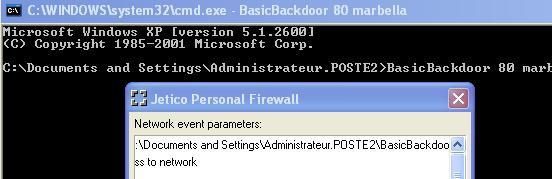
This BackDoor can bypass many firewalls, but not our example (Jetico):
-Gaspar Hooker (R)
-MistaKiller (designed to kill thousands of applications),
-HaxSpy (recent trojan wich uses rootkit technology):


This trojan is really interesting: it tries to bypass the firewall , creates a service and hooks ntdll.
-Kuang (Byweird trojan)
-Morwill trojan clicker
-MSN to CGI
-MSN Pass Sender
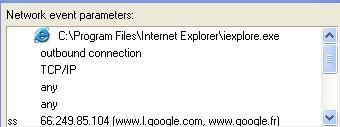
-PhPing (backdoor based ICMP, here's the result of a basic sniff)
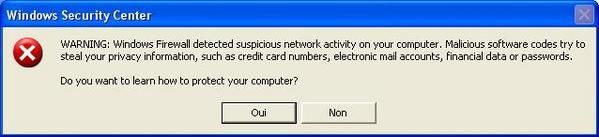
-Registrator (trojan downloader): it looks as an innocent toolbar (many domains), and once executed, it creates files, connects to a site and downloads spyware products: once executed, it modifies IE settings and simultates Windows security center alerts (very funny) and launches IE for products advertising :
-tibs (trojan downloader)
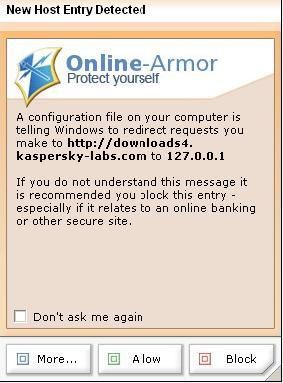
-Try2update (designed to disable antivirus updates by changing host files parameters),
Here a detection with Online Armor:
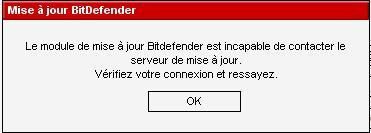
Example with BitDefender:
"BitDefender update engine is unable to contact the update server.
check your connection and try again."
NB. each threat its antidote: PCImmunity is a soft designed to prevent some security engines from being deactivated.
-XPKiller (designed to stop some Windows Security Center functions like the firewall and the automatic updates):
-ZapChast IRC backdoor (available as an "innocent" .gif extension)
b) Worms, virus and scripts:
Feebs, P2P Silly , WormRays , Xorla, Vulcano, V.B Funlove, Autoworm, Ganda, virus;
-script protection:
Here we suppose that the targuet host is not hardened (in a home environment, Windows Scripting Host is not necessary and should be disabled to avoid security risks):
-with Finjan VBS (once executed, it copies documents files and creates a folder on the desktop called "you have been hacked"),
-Dlhello virus, IRC VBS, Vbs Fun love.
-c) spywares/adwares and Cool Web Search pests:
Here we'll try to install some toolbars (generally designed for IE):
www.try2find.com/toolbar/setup/
www.ieplugin.com/download.html
For Firefox: www.voonda.com/toolbar/install.shtml
-180search assistant/adware shop SahaAgent/adware180Solutions
NB.180Searchassistant is classified on the top list of most prevalent spywares by Sunbelt labs.
-d) other malwares (all kind of type)